All Blogs
As TECHAiDE, has been selected to participate in this year’s edition of the Annual Impact Roundtable Discussion (AIRTAD) and Robotics Competition, we extend a special invitation to visit our booth to experience firsthand what we have to offer. The three-day event will take place in the main auditorium of the University of Professional Studies, Accra, from Monday, February 26th, to Wednesday, February 28th, 2024. As leaders in your respective industries, we believe this event will be of great interest to you.
It's super important to keep your computer updated to stay safe, run smoothly, and get the latest cool stuff. Updating your computer helps fix security issues, bugs, and makes it work better. In this blog, we'll talk about updating operating systems like Windows and Windows Defender Antivirus. You can update your computer automatically or do it yourself manually.
In today's tech-driven world, keeping students engaged in the classroom can be a challenge. But what if there was a way to make learning fun and interactive? That's where educational apps and games come in.
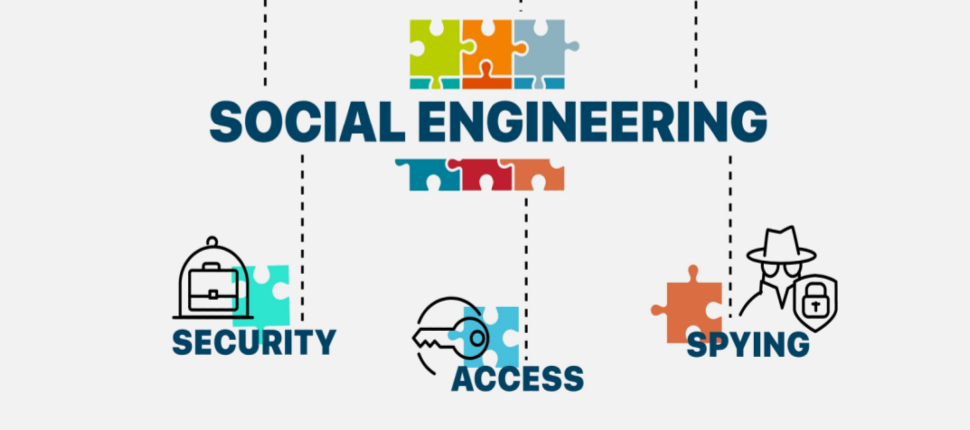
Email phishing is a deceptive cyber attack where malicious actors use fraudulent emails to manipulate individuals into disclosing sensitive information. This comprehensive document aims to provide a deep understanding of email phishing, covering its definition, various types, underlying causes, potential effects, methods of identification, and proactive measures to prevent falling victim to these threats.
An attacker called the school's finance department, claiming to be from the IT department. They said there was a system upgrade or security concern, and that they needed to verify or obtain login credentials to access the school's financial systems. The attacker creates a sense of urgency, saying that there were dire consequences if their request was not fulfilled promptly.
As a student, discover how to maximize your learning experience by effectively managing social media's potential distractions, time consumption, and information overload with these six practical steps.
Gmail Two-Step Verification, also known as 2-Factor Authentication (2FA), is an additional layer of security that adds an extra step to the login process of your Gmail account.
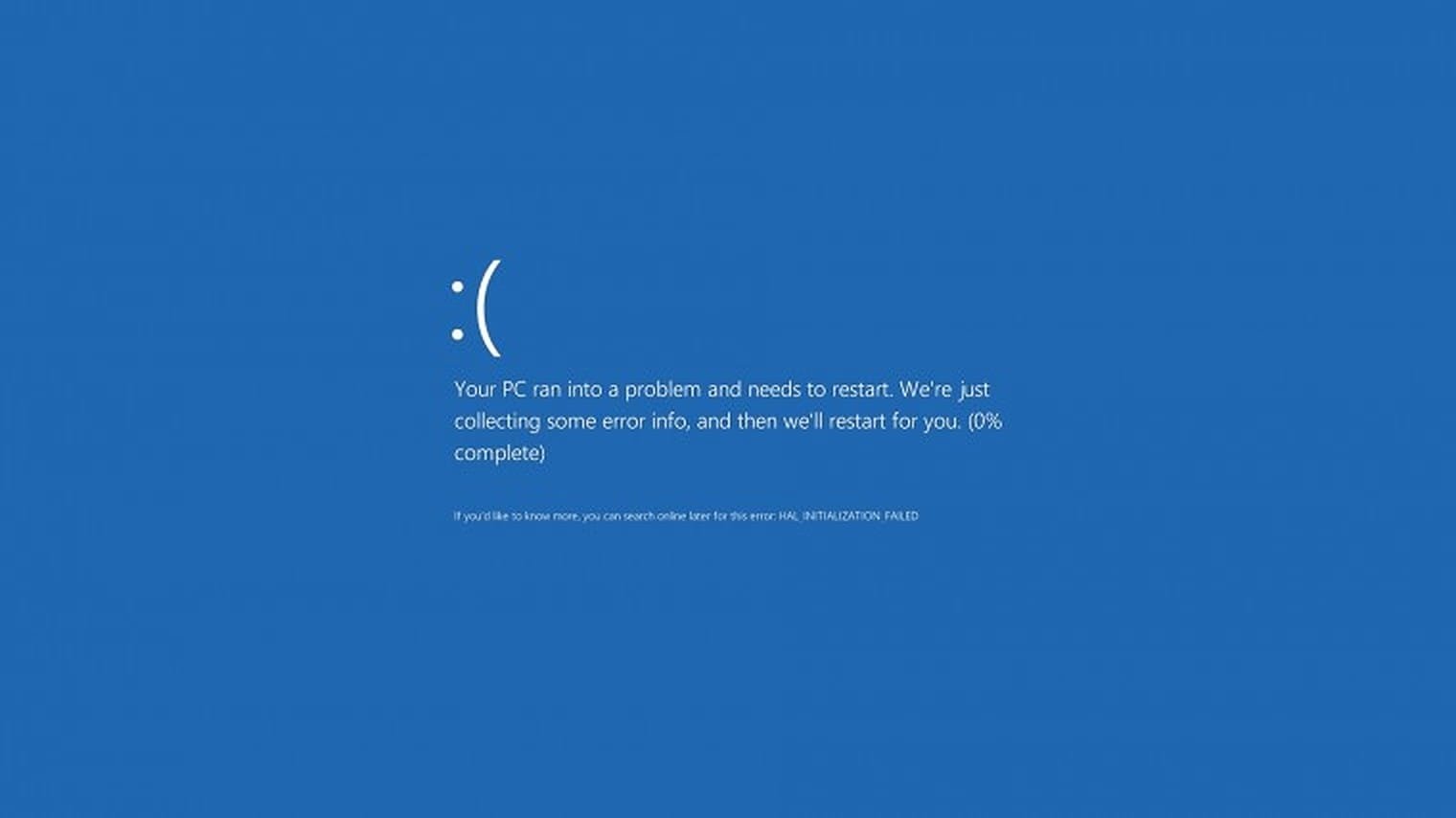
What is a Blue Screen? A Blue Screen, commonly called the Blue Screen of Death, usually appears in Windows 10, Windows 11, or any other versions of Windows when there is an issue with drivers, unstable Central Processing Unit (CPU) performance, or security issues that prevent the Operating System (OS) from functioning properly. It is typically known as a stop error or a fatal system error.
What is two-step verification in WhatsApp? It is an additional feature added to improve security to a WhatsApp account. It helps a WhatsApp user to create and confirm a unique PIN that will be required to access your account.